What happens if we look at IoT as a Network-Of-Things? This is what scientists from the US National Institute of Standards and Technology (NIST) are proposing. Because “there is no formal, analytic or even descriptive set of building blocks that govern the operation, trustworthiness and lifecycle of IoT components” is difficult to assess, monitor, or even resolve cybersecurity, operational and reliability risks that might exist in these systems.
Network-Of_Things (NoT) as the new ‘Science of IoT” The starting point is to look at IoT systems in a new way that breaks down the tasks it performs into four fundamental “components” of the system:
- Sensing;
- Computing;
- Communications;
- Actuation.
To complete the system, we add to these four components and define six “elements” as follows: environment, cost, geographic location, owner, Device_ID, and snapshot, that although are not primitives, are key players in trusting NoTs. These elements play a major role in fostering the degree of trustworthiness5 that a specific NoT can provide.
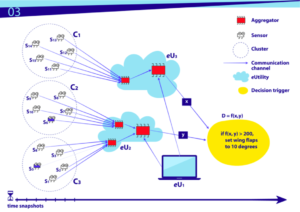
Working with NoTs, Open and Closed: The next step is to apply principles of distributed computing to these components and elements making them networked and making them share messages about tasks to operate efficiently, timely and securely.
Let’s use an automobile as example, to apply the principles of NoT. An automobile has hundreds of sensors, numerous Central Processing Unit (CPU)s, databases such as maps, wired communication channels throughout the car, and without any wireless access between any ‘thing’ in the car to the outside. This example is a closed NoT. Such a NoT mitigates nearly all wireless security concerns such as remotely controlling a car, however there could still be concerns of malware and counterfeit ‘things’ that could result in reduced safety. There are also open NoTs where any ‘thing’ interoperates with any ‘thing,’ in any way, and at any time thus from a “trustworthiness” standpoint, is impossible to assure since the NoT is unbounded.
@elenaneira
Resources: NIST Networks of Things

